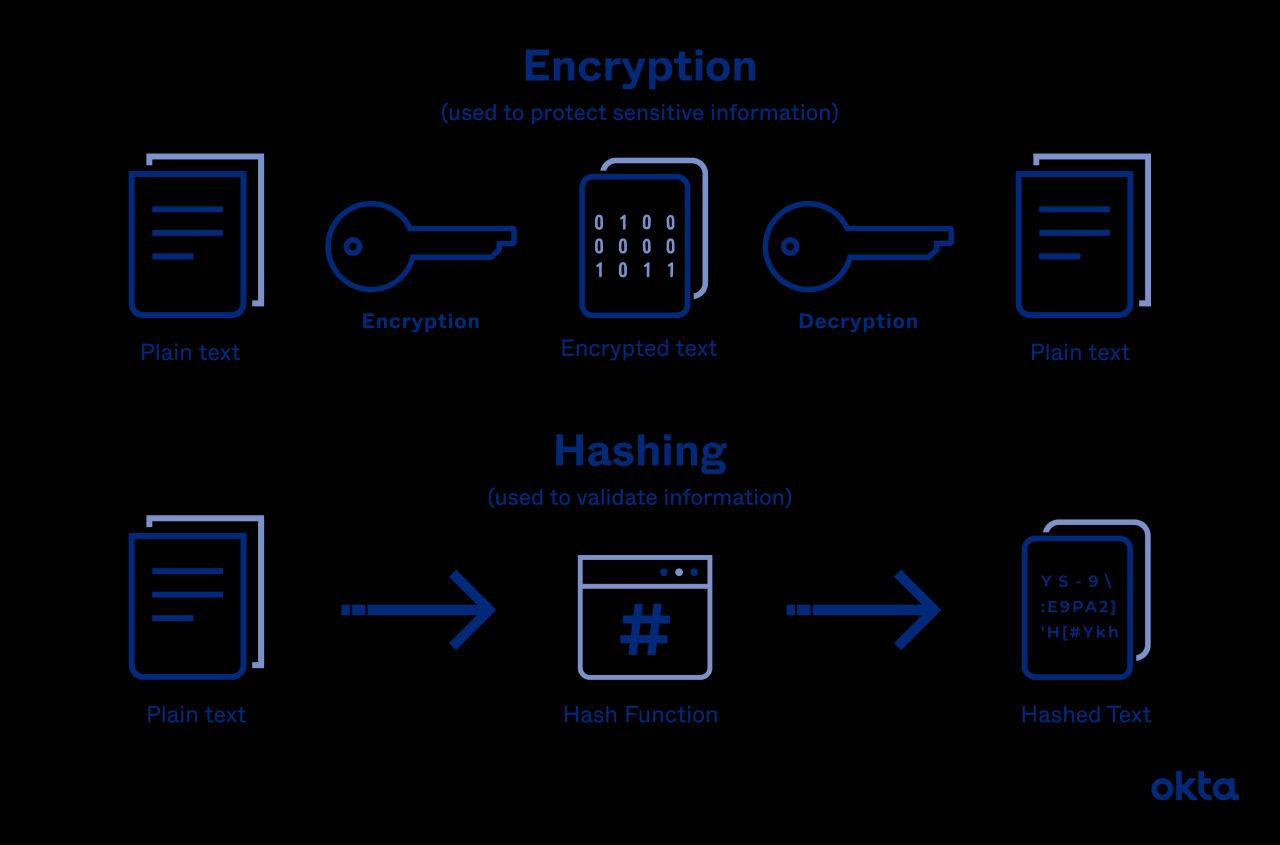
You are using insecure hash algorithm in CA signature, which poses significant risks to your organization. This practice can compromise certificate trust and validation, leading to a range of security vulnerabilities. Understanding these risks and implementing appropriate mitigation strategies is crucial for maintaining the integrity of your digital infrastructure.
In this article, we will delve into the dangers associated with using insecure hash algorithms in CA signatures, explore effective mitigation techniques, and provide guidance on transitioning to more secure algorithms. We will also discuss industry standards and regulations related to this topic and present case studies to illustrate the potential consequences of using insecure hash algorithms.
1. Insecure Hash Algorithms in CA Signature
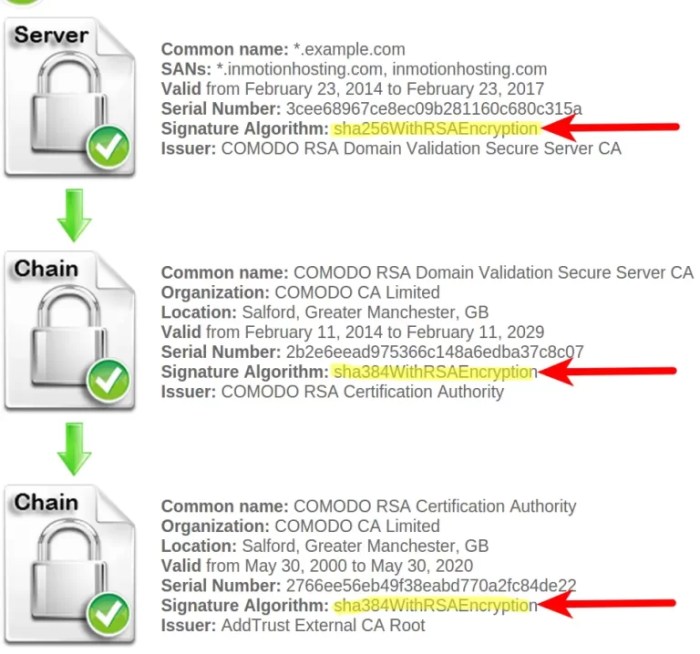
Insecure hash algorithms pose significant risks to the security of certificate authorities (CAs) and the trust placed in their signatures. When used in CA signatures, insecure hash algorithms can allow attackers to forge certificates, impersonate legitimate entities, and compromise the integrity of secure communications.
The impact of insecure hash algorithms on certificate trust and validation is profound. Certificates signed with insecure hash algorithms may be vulnerable to collision attacks, where an attacker can find two different inputs that produce the same hash value. This can allow attackers to create fraudulent certificates that appear to be legitimate, potentially leading to man-in-the-middle attacks and other security breaches.
Examples of insecure hash algorithms include MD5 and SHA-1. MD5 has been deprecated due to its vulnerability to collision attacks, while SHA-1 is also considered insecure and is being phased out by major browsers and operating systems.
Mitigation Strategies
Mitigating the risks associated with insecure hash algorithms in CA signatures requires a multi-pronged approach that includes:
- Transitioning to more secure hash algorithms, such as SHA-256 or SHA-3
- Revoking certificates signed with insecure hash algorithms
- Implementing strong certificate management practices
- Educating users and organizations about the risks of insecure hash algorithms
The transition to more secure hash algorithms is a complex and time-consuming process that requires careful planning and coordination between CAs and their customers. However, it is essential to ensure the long-term security of the public key infrastructure (PKI).
Impact on Certificate Authorities
Insecure hash algorithms have a significant impact on CAs. CAs are responsible for issuing and managing certificates, and they must ensure that their signatures are secure and trustworthy. Using insecure hash algorithms in CA signatures can undermine the trust placed in CAs and their certificates.
CAs have a responsibility to transition to more secure hash algorithms and to revoke certificates signed with insecure hash algorithms. They must also implement strong certificate management practices to ensure the integrity of their certificates.
Industry Standards and Regulations
Industry standards and regulations play a crucial role in ensuring the secure use of hash algorithms in CA signatures. The National Institute of Standards and Technology (NIST) has published guidelines for the use of hash algorithms in PKI, and many countries have adopted these guidelines into their own regulations.
Regulatory bodies are responsible for enforcing industry standards and regulations. They can impose penalties on CAs that fail to comply with these standards, and they can also issue guidance on the use of hash algorithms in CA signatures.
Case Studies, You are using insecure hash algorithm in ca signature
Several organizations have experienced issues related to insecure hash algorithms in CA signatures. In 2017, the security researcher Moxie Marlinspike demonstrated a collision attack against the SHA-1 hash algorithm. This attack raised concerns about the security of certificates signed with SHA-1, and led to the deprecation of SHA-1 by major browsers and operating systems.
In 2020, the security researcher Filippo Valsorda discovered a vulnerability in the OpenSSL library that allowed attackers to forge certificates signed with MD5. This vulnerability was exploited in the wild to create fraudulent certificates that were used in phishing attacks.
FAQ: You Are Using Insecure Hash Algorithm In Ca Signature
What are the risks of using insecure hash algorithms in CA signatures?
Using insecure hash algorithms in CA signatures can compromise certificate trust and validation, making it easier for attackers to impersonate legitimate entities, intercept communications, and access sensitive data.
What are some examples of insecure hash algorithms?
Examples of insecure hash algorithms include MD5, SHA-1, and SHA-224. These algorithms have known vulnerabilities that can be exploited by attackers to generate collisions and compromise the integrity of digital signatures.
What are the best practices for mitigating the risks associated with insecure hash algorithms?
Best practices for mitigating the risks associated with insecure hash algorithms include transitioning to more secure algorithms such as SHA-256 or SHA-512, implementing strong key management practices, and regularly monitoring and updating digital certificates.